I didn’t know these folks!
This project seems to be very interesting.
Thanks for letting know about it!
It shows once again that Storj can really become an Enterprise-grade storage backend component. Plus, this kind of collaboration between 2 innovative projects is beneficial to each of them since it may make the community grow.
Thanks!
It sounds interesting but running their node also sounds like running a Tor exit node. Hmmmm. I don’t know if that’s worth it.
I’m not completely aware of that.
What are the real risks?
It’s similar to creating a guest wifi. You are inviting somebody else to use your IP for whatever. So whatever this person does, it shows your IP. So let’s say somebody uses it to threaten another person, that could get your IP being reported or your place even raided. I don’t like that idea.
Yes, this came to my mind.
But if the node is running on a Datacenter (let’s say AWS), what are the real risks?
I mean: I know the theory but are there any precedents for this kind of use?
I don’t think it is much different. It depends on the charge. The datacenter server might get confiscated, which the datacenter probably would not like very much.
But the datacenter also knows who you are, so they would pass any abuse message to you or if required your contacts to the cops.
I’ve spooled up a node but set it to only have Whitelisted traffic.
It’ll mean less traffic and less reward but I too am cautious of what kind of traffic might pass through my IP, and as I’m running the node at home I would not wish to have the police knocking on my door…
yeah I was just sitting here flashing an SD card to start up one of their nodes, and while reading the FAQs, that’s the part that really doesn’t sit well with me.
I have no interest in making my public IP available, even if the user couldn’t actually see my IP, which I’m not convinced of, I have no interest in the risk of someone doing something they shouldn’t while it’s traceable to my IP…
I’d need their node to have some sort of other VPN in it to hide any traffic going through my node from my ISP for me to be convinced of setting something like this up, which may defeat the entire purpose…
But that seems to be the deal.
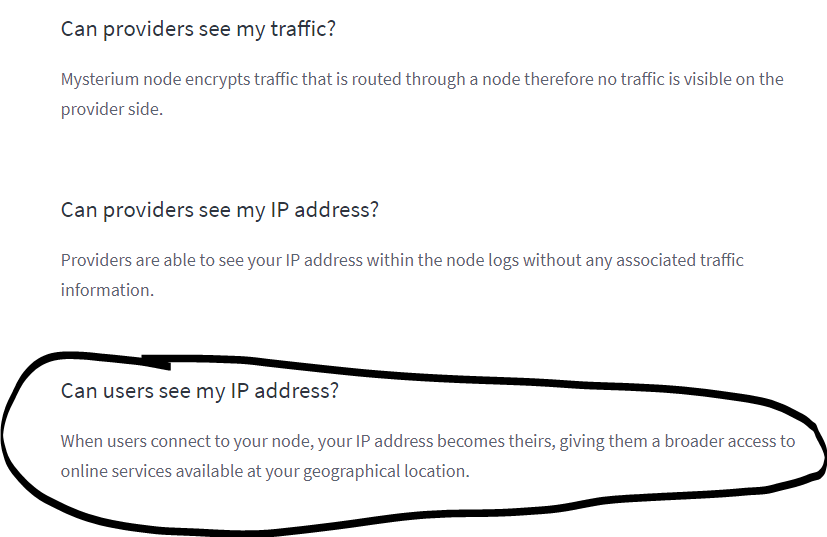
The users absolutely can see your IP.
Right. Although I believe at the end there is exception from liability as you are running this as service provider, but as individual private user they will first focus on you and investigate you, which means, they could raid your home and seize your electronics until you can prove it was not you. I can see no fun in that. That is a huge difference to those companies where it is clear already from their IPs that they are VPN providers.
I can remember that when Tor was not yet well known here, there have been people who have been running Exit Nodes have been raided (some even convicted but later overturned). I don’t need that.
That is obvious a nice thing about Tor, that you can run a relay node, that just passes traffic through, but does not serve as endpoint and it is a bit sad that they have not been able to make some partnerships to get more relay nodes up.
Check this…
If you check to whitelist client only now this is only test traffic from Mysterium Team
And there
Currently all whitelisted traffic is test traffic that comes directly from the Mysterium team and verified B2B partners.
FYI:
Have 25h now on 5 nodes on azure and have 2.5 $ - whitelist turn on
That’s interesting indeed!
Which country is that?